home—lects—exams—hws
D2L—breeze (snow day)
deterlab-startup-instructions
deterlab startup
hw02 prelude
Overview
This document contains (only) instructions for starting up your deterlab machine;
the “real” hw02 instructions, to be carried out on that machine,
are at hw02 treasure/info hunt [see D2L].
deterlab.net is a site which allows you to create
virtual personal machines and even entire networks.
They call such machines/networks an “experiment”.
There are four main steps you'll follow (with detailed instructions below):
-
Log in to deterlab.net and set up your virtual machine (your experiment).
You'll need the deterlab ID and password you were e-mailed
(you might need to check your spam folder; the email will be from deterlab.net).
-
From your local machine, use a putty (or, from mac/linux, a terminal window)
to ssh to deterlab's public server users.deterlab.net.
-
Finally, from that public server, you'll ssh to the individual
machine you created in step I,
and follow the instructions in
hw02 treasure/info hunt [see D2L].
-
Transfer your answer-file back to your local machine, submit it on D2L,
and shut down the deterlab experiment.
Detailed instructions
- Starting the deterlab experiment.
(If deterlab is down for routine maintenance,
I suggest you momentarily skip to part IV,
and prepare by figuring out exactly what you'll type when reach IVb.)
-
Go to the D2L site for this course and download the file
linux_deterlab_intro.ns.
This file is found in Dropbox → hw02-dropbox, as one of the
instruction files.
-
Login to www.deterlab.net,
using the username password you received by email from deterlab Saturday morning.
You'll probably be prompted to change your password immediately upon logging in.
Warning:
Do not lose your password;
I will deduct 2pts from your score,
if I have to manually re-set your deterlab account!
Also, don't use your RU password, or any other sensitive password, on deterlab;
I and other administrators might be able to access them.
- Select Open Experimentation > Begin an Experiment (screenshot below)
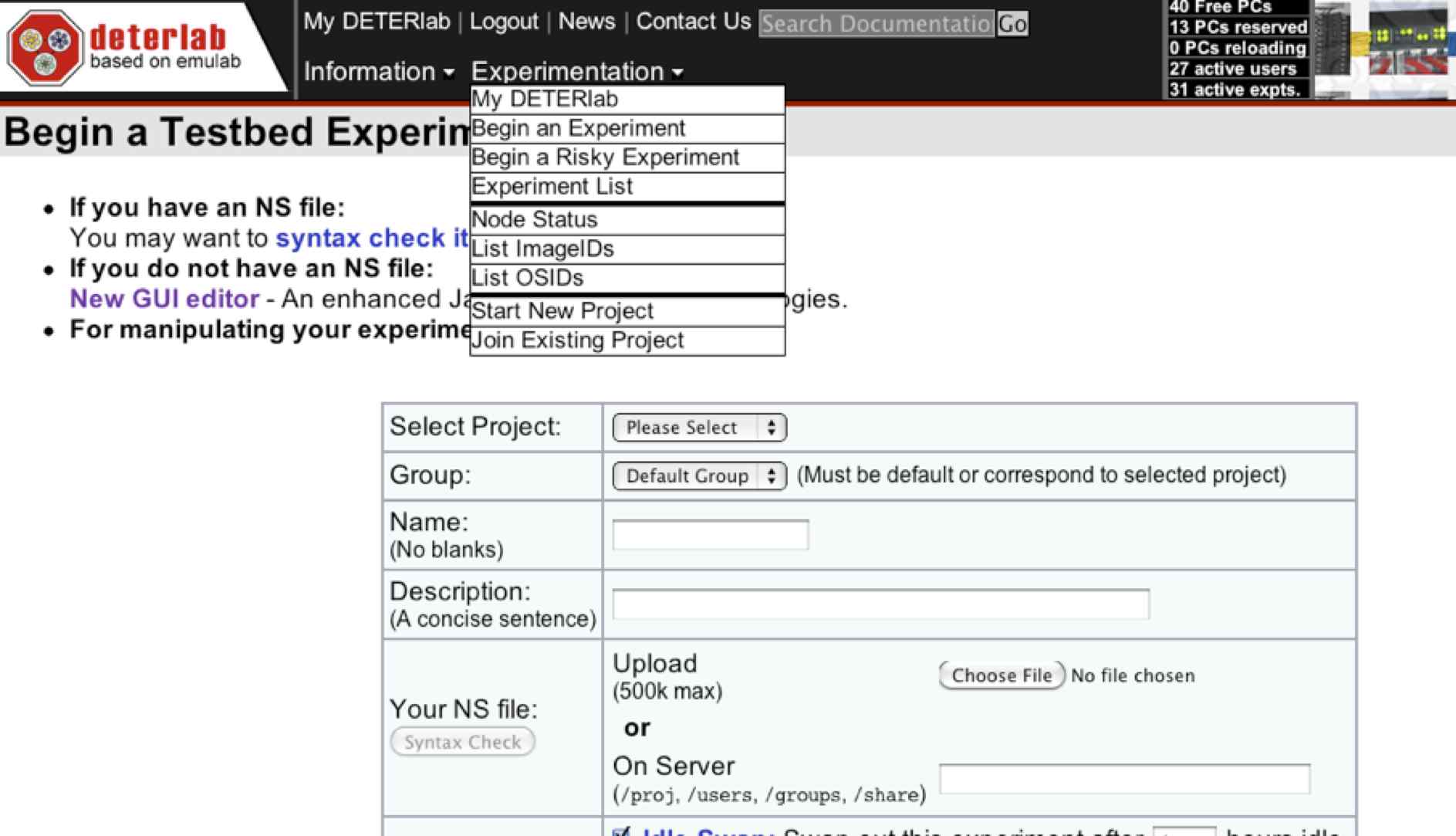
- Fill out the fields as follows:
- Select Project: ITEC245
- Group: Default Group
- Name: yourRUUsername (e.g. ibarland)
This is used (only) in setting up a name for your virtual machine.
In all other places on deterlab, when it asks for a username,
deterlab wants your deterlab username,
something like ru245zz.
- Description: something like “hw02 - linux intro”1.
- Your NS file: Upload the linux_deterlab_intro.ns file that
you downloaded in step I.1.
- Swapping:
- Idle-swap: 3 hours.
(The default is 4 hours, but we are among the kinder, gentler, more polite citizens of Deterlab).
- Max Duration: 12 hours.
Note that after either of these limits,
your “experiment is swapped out” —
that is, the virtual machine along w/ any partial work is destroyed.
Should that somehow happen before you finish, you can start this process over from the beginning.
- Finally, be sure to select the option “Swap In Immediately”.
- Click Submit.
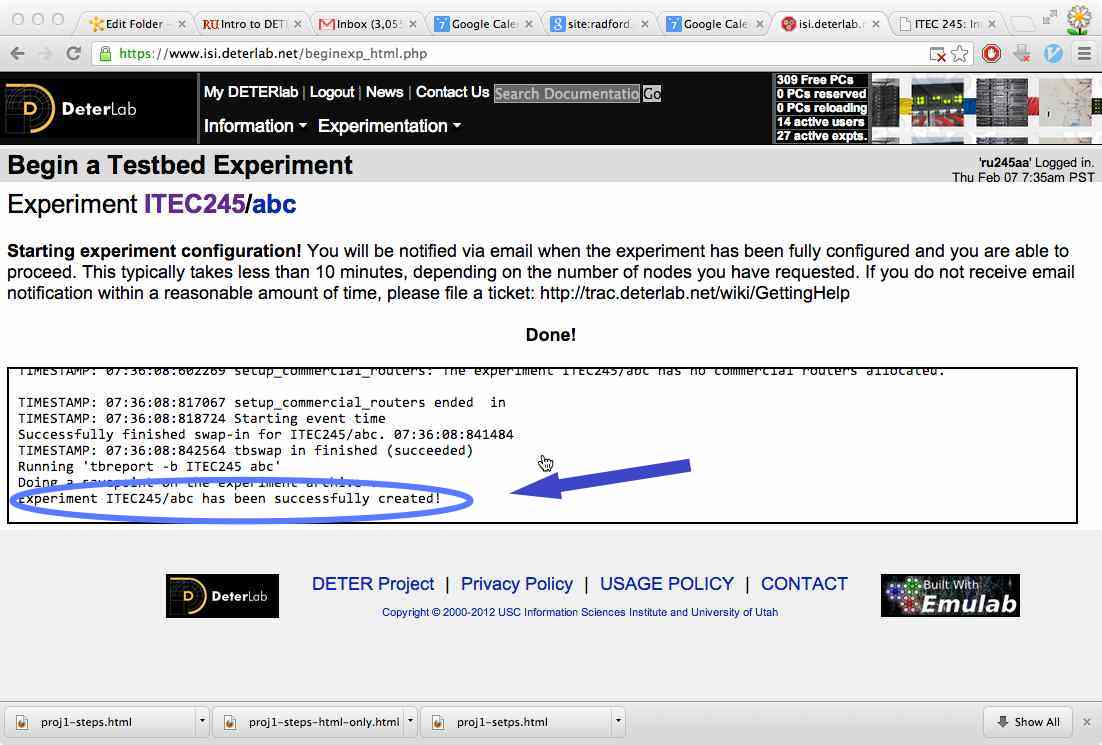
- Wait for a while as Deterlab finds and assigns you a machine,
and configures it (easily two minutes).
You are shown a pane "Working ..." where logging messages scroll by;
it will finish with
“Experiment ITEC245/yourUserId has been successfully created!”
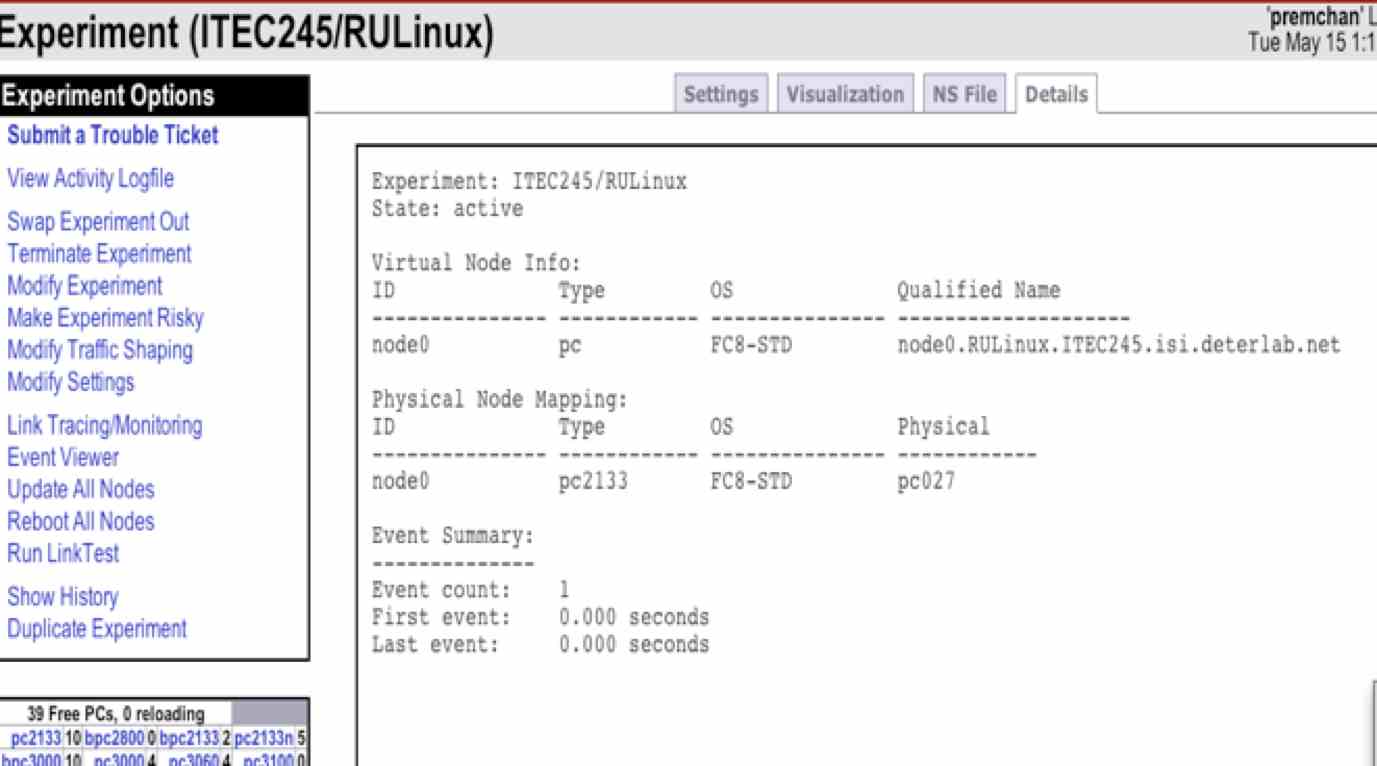
- Go to Experimentation > Experiment List
- Click on your name in the “EID” field
- Click on the Details tab.
You should see something similar to this
(here, the name of the experiment is RULinux; it will be a bit different for you).
 If you don't see this, be sure you really did wait a few minutes!
(Also, if you didn't select “Swap in immediately”, then
nothing will be here.)
If you don't see this, be sure you really did wait a few minutes!
(Also, if you didn't select “Swap in immediately”, then
nothing will be here.)
- Look for the computer name assigned to you.
The blue arrow is pointing to the name assigned to my experiment.
In this example screenshot it is: node0.RULinux.ITEC245.isi.deterlab.net.
You'll need to ssh to this machine below, so I suggest copy/pasting it.
- Log in to the deterlab public server:
Use ssh to log in to users.deterlab.net.
Use your Deterlab username/password.
Using ssh:
If you never remotely logged in to a machine using SSH, don’t panic.
Well, panic just a little, and then read on:
- On Windows:
-
download a program called putty.exe.
You can simply google this program and find a free download page for it.
-
Save putty (on your desktop perhaps), and start it up.
-
In the hostname field: enter users.deterlab.net
- In the username: enter your deterlab username (something like `ru245zz`)
- When prompted for password — guess what you need to enter?
You should now see a terminal window for your linux shell, which is
running on users.deterlab.net.
On Mac or Linux:
- simply fire up a terminal (or start it up).
Look for Applications > Utilities > Terminal on Mac,
or Terminal among the options in Linux.
- Type ssh yourDeterlabUsername@users.deterlab.net
(replace username with your username).
The terminal window will look the same, except now the prompt is
for the linux shell which is running on users.deterlab.net.
(When you exit that shell, you'll be returned to the Terminal window
where you just typed ssh.)
Note that when sshing to a new machine, you'll get a message
similar to:
The authenticity of host some.host.name can't be established.
ECDSA key fingerprint is so:me:lo:ng:he:xa:ha:sh:co:de.
Are you sure you want to continue connecting (yes/no)?
Answer yes
(and ssh will log something like:
Warning: Permanently added some.host.name (ECDSA) to the list of known hosts.).
This is all fine.
Log in to your experiment:
From users.deterlab.net,
ssh into the virtual machine, whose name you copy/pasted in step I.9.
That is, something like ssh node0.RULinux.ITEC245.isi.deterlab.net
Congratulations; you are now the proud part-time leaser of a free Linux machine.
Note that the terminal window you are looking at is the third of a layer:
that shell on your virtual machine is being run from inside
the shell on users.deterlab.net,
which is being run from inside putty (or Terminal).
(Um... Which is being run from your login of the your local machine's OS,
which is being run from the GUI manager of your local machine.2)
So when you finally finish, you'll wrap up by exiting all three layers.
At last, you can begin!
The exact tasks you need to do are in hw02-deterlab-hunt.html [see D2L].
-
The document
starts with some Linux info (much is review;
some is new material but isn't needed for the hw (e.g. screen);
some is new material that is needed for the hw (e.g. find/locate).
-
Then, follow the three tasks (treasure hunt, etc.).
This should leave you with a tarball (a .tar.gz or .tgz file)
in your home directory, on the virtual machine.
Now you just need to submit the answer file, and shut everything down.
-
You'd reasonably think that we need to transfer the file from your virtual machine
(which is not accessible to the general web)
to the gateway users.deterlab.net.
However, you don't actually need to:
Much like your H: drive is mounted onto whatever RU computer you log in to,
similarly your virtual machine's home directory was the same as your users.deterlab.net's
home directory.
So your tarball is already in the home directory of the gateway machine,
you don't need to do anything for this step, yay!
-
We'll copy the file from users.deterlab.net to your local machine.
From your local machine,
3
use scp (Windows/Linux terminal — “secure copy”),
or
putty's copy option
pscp (Windows4)
— “putty secure copy”).
For example
scp ru245zz@users.deterlab.net:myAnswerFile.tar.gz myLocalCopy.tar.gz.
-
Now you can submit that (local) file to the D2L hw02-dropbox.
-
If you haven't already, you can log out of your virtual machine (type exit),
and then out of the shell on users.deterlab.net, and then shut down putty.
-
Although your experiment will eventually time out by itself,
it's good karma to use your web browser to shut it down yourself,
freeing up resources for other students across the country.
Use the
Experimentation > Experiment List > Experiment Options > Terminate Experiment
button
(as visible on the left side of the
screenshot w/ experiment details).
Note that if the experiment does time out,
you'll get an email from deterlab notifying you that it happened.
1This
“description” field is for the Deterlab administrators to let me
know if any experiment has gone rogue.
Since I'm only using deterlab for one class,
it won't be too hard for me to figure out what project they might be
referring to.
↩
2
And I guess the your local hardware is running in The Universe,
as is your brain, which also has a terminal-window into said Universe.
Or, if you're a fan of The Matrix, your brain's terminal window
is getting input some other machine.
↩
3You certainly could run scp to transfer from another machine
to your own computer;
this would require knowing your own computer’s IP address (as from www.whatsmyip.org/).
Also, your machine's OS needs to be configured to accept incoming ssh connections,
and a client needs to be running and listening to the port.
(On a Mac, a client is running by default, but you might need to visit
System Preferences > Sharing > Remote Login,
to make sure a firewall isn’t rejecting all incoming ssh attempts.
Of course, allowing this on your machine opens yourself up to attack,
if they can find/guess an account name and password on your machine.)
For all these reasons, I recommend running scp on your local machine, as
in the main instructions.
↩
4
Instructions for downloading/using pscp on Windows
(based on the “introduction to ssh”, linked from Treasure Hunt point#4):
- download pscp.exe
from (say)
www.chiark.greenend.org.uk/~sgtatham/putty/download.html,
-
open a cmd terminal window on your own Windows machine (Start > Run > cmd),
and
-
type pscp ...arguments....
However, you might need to specify the entire path to pscp.exe,
so that the cmd shell can find it.
For example, something like ./Downloads/pscp ...arguments....
↩
home—lects—exams—hws
D2L—breeze (snow day)






 If you don't see this, be sure you really did wait a few minutes!
(Also, if you didn't select “Swap in immediately”, then
nothing will be here.)
If you don't see this, be sure you really did wait a few minutes!
(Also, if you didn't select “Swap in immediately”, then
nothing will be here.)
